Are you ready to bring more awareness to your brand? Consider becoming a sponsor for The AI Impact Tour. Learn more about the opportunities here.
“Leave a message and we’ll get back to you soon.”
“Read our recent media coverage.”
“Questions? Visit our FAQ page.”
These aren’t messages from corporate websites — although you’ll find them there, too — they’re from extortion gangs.
VB Event
The AI Impact Tour
Connect with the enterprise AI community at VentureBeat’s AI Impact Tour coming to a city near you!
The hacker stereotype is one of a faceless, hoodie-wearing figure hunkered in front of a laptop in a basement somewhere. But modern ransomware gangs are giving this a 180-degree spin: They are increasingly media savvy, actively seeking press coverage, reaching out to journalists and even granting interviews.
Previously, “the idea of attackers regularly putting out press releases and statements — let alone giving detailed interviews and arguing with reporters — was absurd,” Sophos X-Ops researchers write in a recent report.
Today, though, “far from shying away from the press…some ransomware gangs have been quick to seize the opportunities it affords them.”
Mounting attacks, ever more brazen tactics
Ransomware is rampant, targeting tech giants, casinos, healthcare facilities and everything in between.
An estimated 73% of organizations worldwide were impacted by ransomware attacks in 2023 and the average payment is $1.54 million. The White House has even called ransomware a threat to national security.
Ransomware gangs are thriving and growing ever bolder with their tactics. Beyond announcing hacks and publicly shaming organizations, they are ratting out companies to the Securities and Exchange Commission (SEC). For example, the Black Cat group recently snitched on MeridianLink when they didn’t pay — threatening class action lawsuits and launching bug bounty programs that pay for Personally Identifiable Information (PII) on high-profile individuals and web exploits.

More recently, they have charted even more alarming territory by resorting to threats of physical violence. Microsoft research on the Octo Tempest group, for instance, shared screenshots from hackers to specific targets demanding corporate logins or else “I’m gonna send someone over there at a random time…when ur sleeping…u won’t know when.”
Additionally, they are performing virtual kidnapping and sextortion through the use of advanced voice cloning techniques, deepfakes and manipulated photos and videos.
At the same time, the cybercrime gig economy is easier than ever to get into, thanks to the proliferation of ransomware-as-a-service kits that sell for monthly subscription fees of just $40 and come with quickstart guides.
Ransomware gangs are aggressively pursuing “commoditization and professionalization,” according to Sophos X-Ops researchers. They are seeking “notoriety, egotism, credibility” and aim to ‘mythologize’ themselves by engaging with the press, while also controlling the narrative, increasing pressure on victims and using media coverage as a platform to reach fresh recruits.
“Ransomware gangs are aware that their activities are considered newsworthy, and will leverage media attention both to bolster their own ‘credibility’ and to exert further pressure on victims,” researchers said.
Branding, PR best practices
Today’s media-savvy ransomware groups have dedicated private PR channels; leak sites with FAQs, message forms, help centers and news about upcoming data releases; and even invite reporters to reach out.
Branding is a key element; beyond their edgy, ominous and memorable names, gangs develop dedicated logos and eye-catching graphics — from Anime-style to retro neon to colorful bubbly lettering.
The threat actor Vice Society, for instance, introduces itself: “Hello everyone! We’ve decided to start our own blog. Here you will see some news about us, our comments about it, etc.”
The group goes on to thank a journalist for naming them among the top 5 ransomware groups in 2022, and also offers a cheery (and ironic): “With love!” It further provides a request form for journalists and questions it won’t answer — such as location, ages and preferred vulns/CVEs. Its FAQs section details how long it’s been in operation (“from January 2021”), why it started (“a group of friends that were interested in pen test”) and what it does if laws prevent payment (“we don’t care about laws”).
Vice Society also pledges to try to respond to queries within 24 hours, which Sophos X-Ops researchers call “an example of professional PR best practice, which demonstrates how important this is to the threat actor.”
Similarly, data extortion gang RansomHouse states on its site: “We highly respect the work of journalists and consider information accessibility to be our priority. We have a special program for journalists which includes sharing information a few hours or even days before it is officially published on our news site and Telegram channel.”
Other threat actors threaten to leak details to the media should victims fail to pay. One user on a prominent criminal forum reported that negotiations with one organization had broken down and that they would hand over the “entire negotiation exchanges” to “verified press or researchers.”
“Ransomware gangs are very aware that they can exert additional pressure on victims by raising the specter of media interest,” write Sophos X-Ops researchers.
Press releases straight from the source
While it would seem that many hackers, even as they seek media attention, would prefer to remain personally anonymous, some are giving deep-dive interviews to journalists and researchers, including The Record.
Hacker Mikhail Matveev even provided a selfie of himself to the Recorded Future news site and brazenly commented: “There is no such money anywhere as there is in ransomware.”
Sophos X-Ops researchers report that “in most of these interviews, the threat actors seem to relish the opportunity to give insights into the ransomware ‘scene,’ discuss the illicit fortunes they’ve amassed and provide ‘thought leadership’ about the threat landscape and the security industry.”
Similarly, some ransomware groups will offer “press releases.” Data extortion group Karakurt, for its part, maintains a separate page for such news announcements that detail specific attacks, call for recruits and contain direct quotes from “the Karakurt team.”

Others use releases to rebrand themselves or elevate their so-called ethics above other groups and even victim organizations taking protective measures.
In an announcement “for immediate release,” the group Royal Data Services pledges not to publish data from an educational institution and will instead delete it “in line with our stringent data privacy standards and as a demonstration of our unwavering commitment to ethical data management.”
Sophos X-Ops researchers underscore the language mimicking public statements, such as “bedrock principles upon which Royal Data Sciences operates” and “we respect the sanctity of educational and healthcare services.”
Then there’s the other side of the coin: Ransomware gangs use public platforms to shame outlets or even specific reporters.
One press release from the group Snatch admonishes the media for reporting incorrect facts: “We see the same mistake…that the media report year after year, without bothering to check the data and study the history of the project.”
ALPHV/BlackCat, similarly, published a 1,300-word post criticizing numerous news sites for “not checking sources and reporting incorrect information.”
CL0P — which was responsible for the MOVEit file transfer system breach, considered to be one of the most significant (and ongoing) in recent history — specifically called out the BBC for “creating propaganda” after the ransomware group provided information to the outlet.
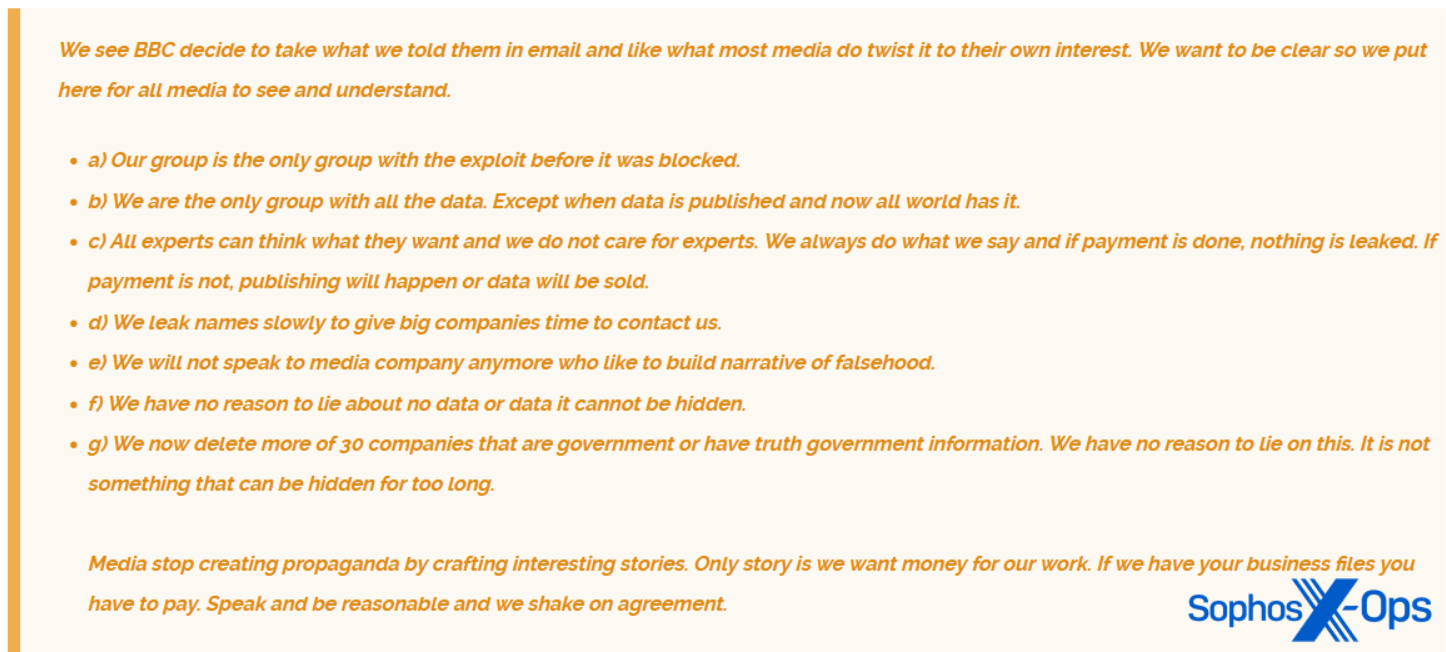
Sophos X-Ops researchers call this an attempt to ‘set the record straight,’ by representing itself as the only authoritative source of information. The report also notes that mistrust is common in criminal forums, even as ransomware campaigns by their very nature require going public (at the very least to their victim).
But whether they consider the media to be friend, foe — or something in between — there’s no doubt that “ransomware actors are on their way to becoming public figures,” researchers assert. “Accordingly, they are devoting an increasing amount of time to ‘managing the media.’’
These extortionists are “conscious that cultivating media relationships is useful for achieving their own objectives and refining their public image.”
The report concludes: “It may be a way off, but it’s not unfeasible that in the future, ransomware groups may have dedicated, full-time PR teams: copywriters, spokespeople, even image consultants.”
VentureBeat’s mission is to be a digital town square for technical decision-makers to gain knowledge about transformative enterprise technology and transact. Discover our Briefings.










